
The Netgear device is vulnerable to a command injection in the “samba_writeEtcPasswd” function, which is reachable only if a USB storage device is plugged into the router. A root shell may be obtained by exploiting this vulnerability.
The exploitable router configuration looks like the following image. Note the USB plugged in near the upper right corner. The router is restarted in this configuration. No other changes were made to the router configuration.
The following screenshot portrays where the command injection takes place.
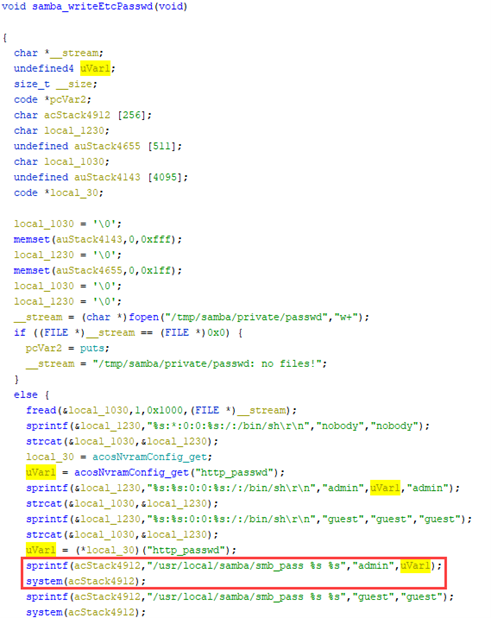
In the above screenshot, the “http_passwd” variable is obtained from NVRAM. This value is stored in uVar1, which is then used as an argument to the “smb_pass” program. This program is executed using a “system()” function.
After the administrator password is changed, another function “usbRestartServices” is called. “usbRestartServices” then calls “samba_writeEtcPasswd” if a USB device is plugged in. This is depicted in the following screenshot.
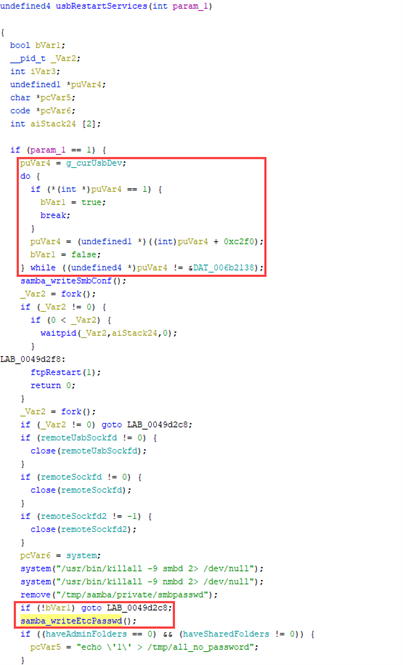
Note that “puVar4” is set to a variable which holds a reference to the current USB Device. If it is present (plugged in), “bVar1” is set to Boolean true. If so, the if-statement right above the “samba_writeEtcPasswd()” function call does not jump to a different label, thereby calling the affected function.
Here's the weaponized PoC. It authenticates using default creds, changes the password (while including the command injection), triggers the vuln (just by changing it, it will trigger), and then changes it back.
Here's a video demonstrating exploitation.
This vuln / router are probably too old for Netgear to give a shit, and I'm not interested in their bug bounty program for older routers which involves "kudos" and not publishing the vuln, as it may make for an interesting case study for manual analysis (educational purposes). The vuln is not high-impact, since it's LAN-side, authenticated, and a USB device must be plugged in, but it's a fun short demo of the benefits of manual analysis. Moreover, this vuln can be used to load a remote debugger onto the router which can allow for debugging more complex bugs without having to fiddle with UART or the hardware in general.
-Faisal